PHP — OpenSSL Functions
OpenSSL is a free open source module that is meant to take care of communications that takes place over computer networks. OpenSSL is a tool for Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols.
What is an SSL Certificate?
A Secure Sockets Layer i.e SSL is used by website.The SSL certificate takes care of protecting the data between two computers by using ecryption. The two computers involved can be the data sharing between client and server. When you share data like password, credit card details, home address, social security number it has to be protected and the same is taken care by the SSL certificate.The SSL certificates makes sure the identity of both computers involved is authenticated for safe connection.
OpenSSL installation in PHP
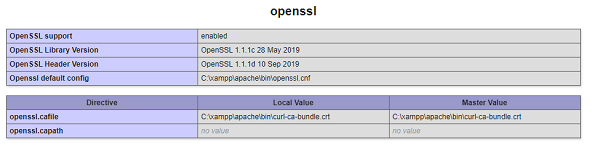
OpenSSL module is by default added to PHP. You can activate the same by removing the (;) ;extension=php_openssl.dll added at the start of the extension in php.ini. After that restart apache and to confirm if the changes are reflecting save below code as .php and execute the .php in browser.
You should see the openssl enabled in the browser as shown below:
OpenSSL configuration
The openssl.cnf is the configuration file and has all the default configuration required for openssl to work.To execute openssl the first thing is that php will try to locate the config file.To get the same you will have to add the php folder to environment variable.
If you are Windows user following are the steps to setup environment variable for php folder:
1. Right click My Computer and go to Properties.
2. Go to Advanced system Settings.
3. Click on the ‘Environment Variables’ button.
4. Edit the path variable and click on Edit button.
5. Now add the Php folder path at the end.I am using xampp so my php folder is C:\xampp\php;
6.Once done click on Ok button.
7.Now open your command prompt and enter the command: openssl version -a.
C:\Windows\system32>openssl version -a OpenSSL 1.0.2l 25 May 2017 built on: reproducible build, date unspecified platform: mingw64 options: bn(64,64) rc4(16x,int) des(idx,cisc,2,long) idea(int) blowfish(idx) compiler: x86_64-w64-mingw32-gcc -I. -I.. -I../include -D_WINDLL -DOPENSSL_PIC -DOPENSSL_THREADS -D_MT -DDSO_WIN32 -static-libgcc -DL_ENDIAN -O3 -Wall -DWIN32_ LEAN_AND_MEAN -DUNICODE -D_UNICODE -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DO PENSSL_BN_ASM_MONT5 -DOPENSSL_BN_ASM_GF2m -DRC4_ASM -DSHA1_ASM -DSHA256_ASM -DSH A512_ASM -DMD5_ASM -DAES_ASM -DVPAES_ASM -DBSAES_ASM -DWHIRLPOOL_ASM -DGHASH_ASM -DECP_NISTZ256_ASM OPENSSLDIR: "/etc/ssl"
Now php will be able to locate the openssl.cnf configuration file.
OpenSSL functions
Following table lists down all the functions related to PHP OpenSSL. Here column version indicates the earliest version of PHP that supports the function.
| Sr.No | Function & Description | Version |
|---|---|---|
| 1 | openssl_pkey_new() |
Returns a resource identifier that has new private and public key pair
Exports the key to a file
Encrypts the data with the private key
Encrypts the data with public key
Decrypts the data with the public key
Decrypts the data with the private key
OpenSSL
I was having a heck of a time finding help on making asynchronous encryption/decryption using private key/public key systems working, and I had to have it for creating a credit card module that uses recurring billing.
You’d be a fool to use normal, ‘synchronous’ or two-way encryption for this, so the whole mcrypt library won’t help.
But, it turns out OpenSSL is extremely easy to use. yet it is so sparsely documented that it seems it would be incredibly hard.
So I share my day of hacking with you — I hope you find it helpful!
if (isset( $_SERVER [ ‘HTTPS’ ]) )
echo «SECURE: This page is being accessed through a secure connection.
» ;
>
else
echo «UNSECURE: This page is being access through an unsecure connection.
» ;
>
// Create the keypair
$res = openssl_pkey_new ();
// Get private key
openssl_pkey_export ( $res , $privatekey );
// Get public key
$publickey = openssl_pkey_get_details ( $res );
$publickey = $publickey [ «key» ];
echo «Private Key: $privatekey
Public Key: $publickey » ;
$cleartext = ‘1234 5678 9012 3456’ ;
echo «Clear text:
$cleartext » ;
openssl_public_encrypt ( $cleartext , $crypttext , $publickey );
echo «Crypt text:
$crypttext » ;
openssl_private_decrypt ( $crypttext , $decrypted , $privatekey );
echo «Decrypted text: $decrypted
» ;
?>
Many thanks to other contributors in the docs for making this less painful.
Note that you will want to use these sorts of functions to generate a key ONCE — save your privatekey offline for decryption, and put your public key in your scripts/configuration file. If your data is compromised you don’t care about the encrypted stuff or the public key, it’s only the private key and cleartext that really matter.
For checking the status of a client certificate using OCSP, you can use this script:
// User variables:
$dir = ‘/path/to/temp/’ ; // Directory where apache has access to (chmod 777).
$RootCA = ‘/path/to/Root.cer’ ; // Points to the Root CA in PEM format.
$OCSPUrl = ‘http://ocsp.url’ ; //Points to the OCSP URL
// Script:
$a = rand ( 1000 , 99999 ); // Needed if you expect more page clicks in one second!
file_put_contents ( $dir . $a . ‘cert_i.pem’ , $_SERVER [ ‘SSL_CLIENT_CERT_CHAIN_0’ ]); // Issuer certificate.
file_put_contents ( $dir . $a . ‘cert_c.pem’ , $_SERVER [ ‘SSL_CLIENT_CERT’ ]); // Client (authentication) certificate.
$output = shell_exec ( ‘openssl ocsp -CAfile ‘ . $RootCA . ‘ -issuer ‘ . $dir . $a . ‘cert_i.pem -cert ‘ . $dir . $a . ‘cert_c.pem -url ‘ . $OCSPUrl );
$output2 = preg_split ( ‘/[\r\n]/’ , $output );
$output3 = preg_split ( ‘/: /’ , $output2 [ 0 ]);
$ocsp = $output3 [ 1 ];
echo «OCSP status: » . $ocsp ; // will be «good», «revoked», or «unknown»
unlink ( $dir . $a . ‘cert_i.pem’ );
unlink ( $dir . $a . ‘cert_c.pem’ );
?>
It can be ameliorated, but it’s just a beginning!
Normally, you can extract the ocsp url from the client certificate. Also, an OCSP request contains only the hash of the issuer name, the hash of the issuer’s key, and the serial number of the client certificate. All three can be extracted directly from the client certificate.
In regards to the comment above:
«After generating a key pair with OpenSSL, the public key can be stored in plain text format. I then encrypted the private key itself using regular mcrypt with the human-memorizable key of my choice and converted it to ACSII using base64_encode. Then to get the private key back, I just decrypted it with mcrypt. This way I could store the encrypted private key on the server without worrying about having things stored unencrypted. «
To anyone reading this that might not be all that familiar with public key cryptography; I haven’t the slightest idea what this person is talking about, but I can tell you its an absolutely horrible idea. He might have ended up with something that «looked like a private key» insofar as it was a base64 encoded string, but he did not have a private key. The parameters that make up a public/private key pair are EXTREMELY specific and in the case of RSA rely on very large co-primes plus an even larger moduli. Its not just a base64 encoded string; and just for the record. base64 encoding is not encryption.
One of two things happened; the more likely is the whatever program he needed the certificate for realized there was something wrong with the private key, and ignored it, reverting to either a default key, or null encryption or something. The worse outcome would be if it interpreted whatever was there as legitimate; and encrypted data as if it were a a proper certificate; encrypting this way would likely provide close to zero security and I’m not even sure you could decrypt the data once encrypted. Its not worth giving much thought.
You can read about pki certificate structures and attribute frameworks by pasting «T-REC-X.509-201210-I» into your favorite interwebs search widget and following the result to the International Telecommunications Union webpage, or you can refer to the numerous RFCs; 6818, 5820 being good places to start. The Internet Engineering Task Force archives all RFCs, but there are other sources as well. «IETF RFC» should be enough to get you there.
. sorry, the «spam buster» was giving me all kinds of issues.