- Saved searches
- Use saved searches to filter your results more quickly
- License
- PacktPublishing/Python-Ethical-Hacking
- Name already in use
- Sign In Required
- Launching GitHub Desktop
- Launching GitHub Desktop
- Launching Xcode
- Launching Visual Studio Code
- Latest commit
- Git stats
- Files
- README.md
- Ethical Hacking with Python
- Why Python Programming For Hacking
- How Password Are Hacked
- Ethical Hacking Tutorials
Saved searches
Use saved searches to filter your results more quickly
You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. Reload to refresh your session. You switched accounts on another tab or window. Reload to refresh your session.
Python Ethical Hacking, published by Packt
License
PacktPublishing/Python-Ethical-Hacking
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Name already in use
A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?
Sign In Required
Please sign in to use Codespaces.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching GitHub Desktop
If nothing happens, download GitHub Desktop and try again.
Launching Xcode
If nothing happens, download Xcode and try again.
Launching Visual Studio Code
Your codespace will open once ready.
There was a problem preparing your codespace, please try again.
Latest commit
Git stats
Files
Failed to load latest commit information.
README.md
Python Ethical Hacking from Scratch
This is the code repository for Python Ethical Hacking from Scratch, published by Packt.
Python Ethical Hacking from Scratch, published by Packt
Penetration testing enables you to evaluate the security or strength of a computer system, network, or web application that an attacker can exploit. With this book, you’ll understand why Python is one of the fastest-growing programming languages for penetration testing. You’ll find out how to harness the power of Python and pentesting to enhance your system security.
This book covers the following exciting features:
- Understand the core concepts of ethical hacking
- Develop custom hacking tools from scratch to be used for ethical hacking purposes
- Discover ways to test the cybersecurity of an organization by bypassing protection schemes
- Develop attack vectors used in real cybersecurity tests
- Test the system security of an organization or subject by identifying and exploiting its weaknesses
- Gain and maintain remote access to target systems
- Find ways to stay undetected on target systems and local networks
If you feel this book is for you, get your copy today!
Instructions and Navigations
All of the code is organized into folders. For example, Chapter02.
The code will look like the following:
subprocess.run( ["ifconfig", "eth0"], shell=True, ) Following is what you need for this book: If you want to learn ethical hacking by developing your own tools instead of just using the prebuilt tools, this book is for you. A solid understanding of fundamental Python concepts is expected. Some complex Python concepts are explained in the book, but the goal is to teach ethical hacking, not Python.
With the following software and hardware list you can run all code files present in the book (Chapter 1-9).
Software and Hardware List
| Chapter | Software required | OS required |
|---|---|---|
| 1-9 | Python version 3.8 | Windows, Mac OS X, and Linux (Any) |
| 1-9 | VMware/Virtualbox | Windows, Mac OS X, and Linux (Any) |
| 1-9 | Visual Studio Code IDE | Windows, Mac OS X, and Linux (Any) |
We also provide a PDF file that has color images of the screenshots/diagrams used in this book. Click here to download it.
- Mastering Python for Networking and Security — Second Edition [Packt][Amazon]
- Mastering Python Networking — Third Edition [Packt][Amazon]
Fahad Ali Sarwar Fahad has been teaching ethical hacking and penetration testing on different online platforms with a solid student base. He’s passionate about cybersecurity and ethical hacking tool development. Fahad is particularly enthusiastic about Python for its simplicity and ease of use and in this book he has chosen it as a language of preference due to its features.
If you have already purchased a print or Kindle version of this book, you can get a DRM-free PDF version at no cost.
Simply click on the link to claim your free PDF.
Ethical Hacking with Python
As a Computer Science Engineer who encrypts the world, one should know how Hacking activities are done. And we must stand front in protecting our world from cybercriminals.
Being able to gain access to a system that you’re not supposed to have access to is known as Hacking. For example, login into an email account without authorization is considered hacking that account. Gaining access to a remote computer without authorization is hacking that computer. So you can see that there are a large number of ways to hack into a system and the word hacking can refer to a number of things but the main concept is the same. Gaining access or being able to do things that you’re not supposed to be able to do, is considered hacking.
Ethical hacking:
To crack passwords or to steal data? No, it is much more than that. Ethical hacking is to scan vulnerabilities and to find potential threats on a computer or networks. An ethical hacker finds the weak points or loopholes in a computer, web applications or network and reports them to the organization. So, let’s explore more about Ethical Hacking step-by-step.
- Black hat hackers:
Here, the organization doesn’t allow the user to test it. They unethically enter inside the website and steal data from the admin panel or manipulate the data. They only focus on themselves and the advantages they will get from the personal data for personal financial gain. They can cause major damage to the company by altering the functions which lead to the loss of the company at a much higher extent. This can even lead you to extreme consequences. - White hat hackers:
Here, we look for bugs and ethically report it to the organization. We are authorized as a user to test for bugs in a website or network and report it to them. White hat hackers generally get all the needed information about the application or network to test for, from the organization itself. They use their skills to test it before the website goes live or attacked by malicious hackers. - 3.Grey hat hackers:
They sometimes access to the data and violates the law. But never have the same intention as Black hat hackers, they often operate for the common good. The main difference is that they exploit vulnerability publicly whereas white hat hackers do it privately for the company.
Note: To know more about types of hackers click here.
Why Python Programming For Hacking
Python is a widely used general-purpose, high-level programming language. Python is a very simple language yet powerful scripting language, it’s open-source and object-oriented and it has great libraries that can be used for both for hacking and for writing very useful normal programs other than hacking programs. In the future and present era python is very popular and it’s easy to learn, learning to hack with python will be fun and you will learn python programming in the best way. There is a great demand for python developers in the market.
Note: To know more about python click here.
How Password Are Hacked
Everyone knows that passwords are not stored a plain text in the website’s database. Now we are going to see how to hack a plain text password when you find a password that is in hashed(md5) format. So we take the input_hash(hashed password in the database) and try to compare it with md5 hash of every plain text password which is in a password file(pass_doc) and when the hashes are matched we simply display the plain text password which is in the password file(pass_doc). If the password is not present in the input password file it will say password is not found, this happens only if buffer overflow doesn’t occur. This type of attack can be considered as a dictionary attack.
Below is the implementation. Let’s suppose the text file containing list of password is password.txt.
Ethical Hacking Tutorials
Master Ethical Hacking with Python by building 35+ Tools from scratch. Get your copy now!
Learn how to develop your own ethical hacking tools using Python, including password crackers, brute force scripts, information gathering tools, sniffing and much more.
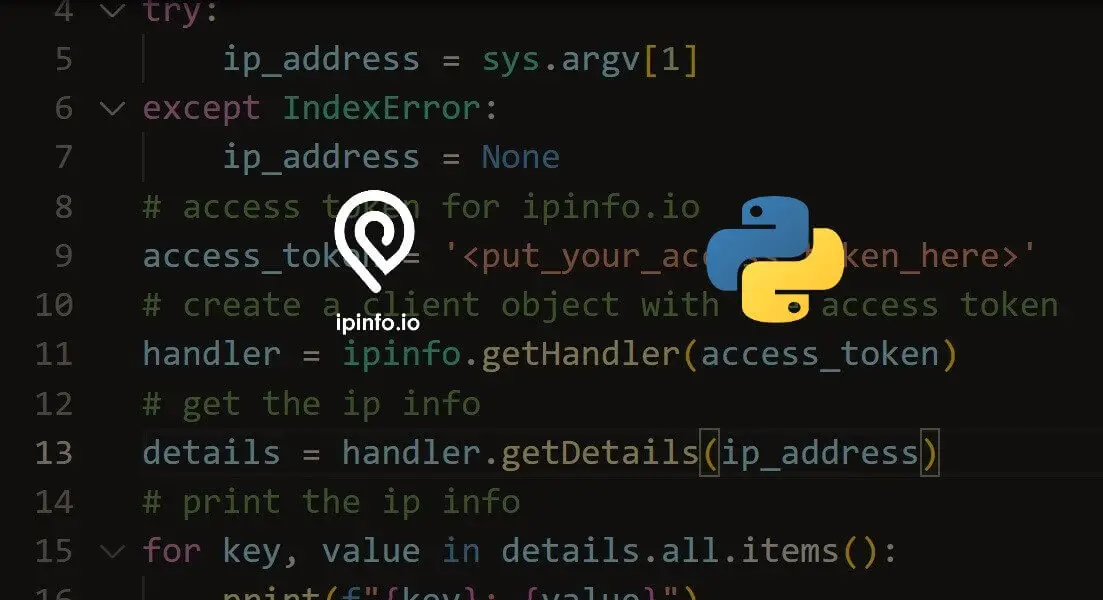
How to Geolocate IP addresses in Python
Learn how you can convert an IP address into a geographic location using IPInfo service and its wrapper in Python.
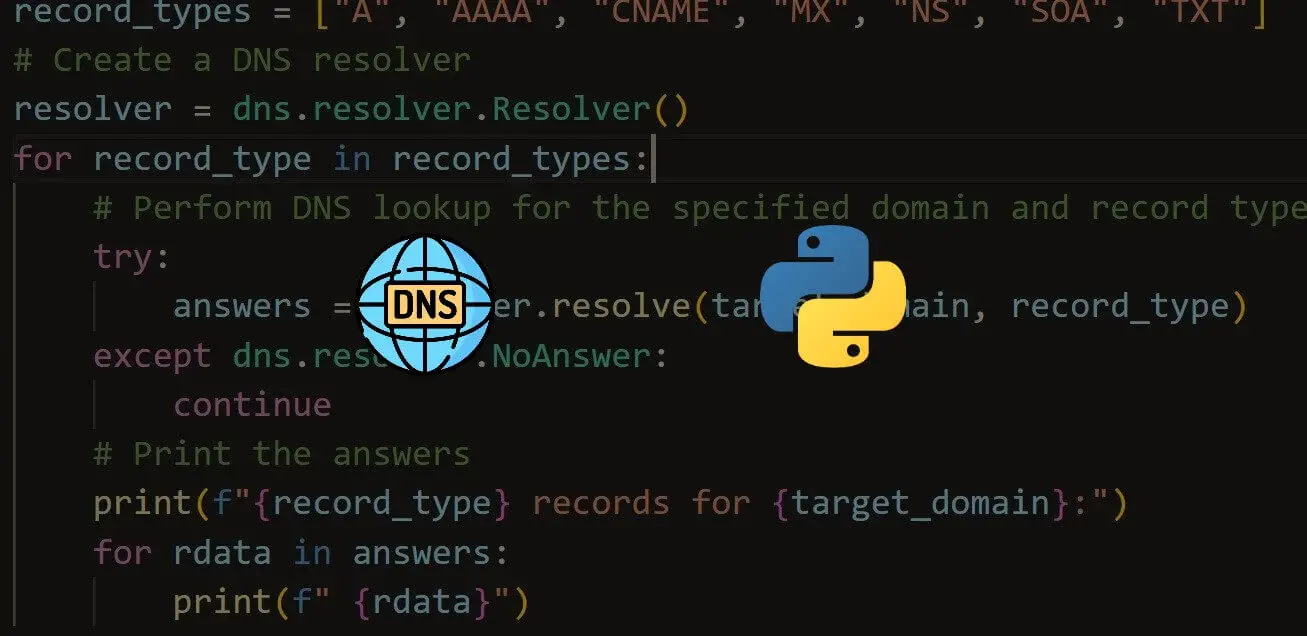
How to Perform DNS Enumeration in Python
Learn how you can extract DNS information of a domain name such as nameservers, IP addresses, email services and more using dnspython library in Python.
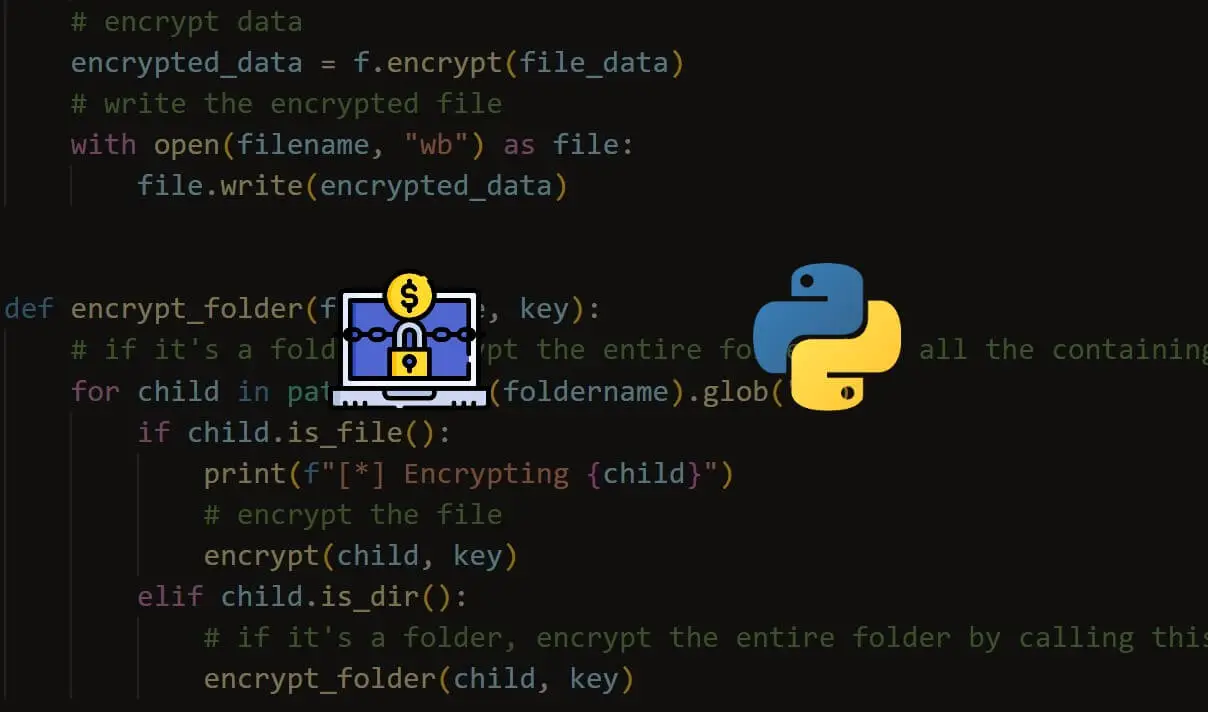
How to Make a Ransomware in Python
Learn how to build a ransomware using symmetric encryption (AES algorithm) with the help of cryptography library in Python.
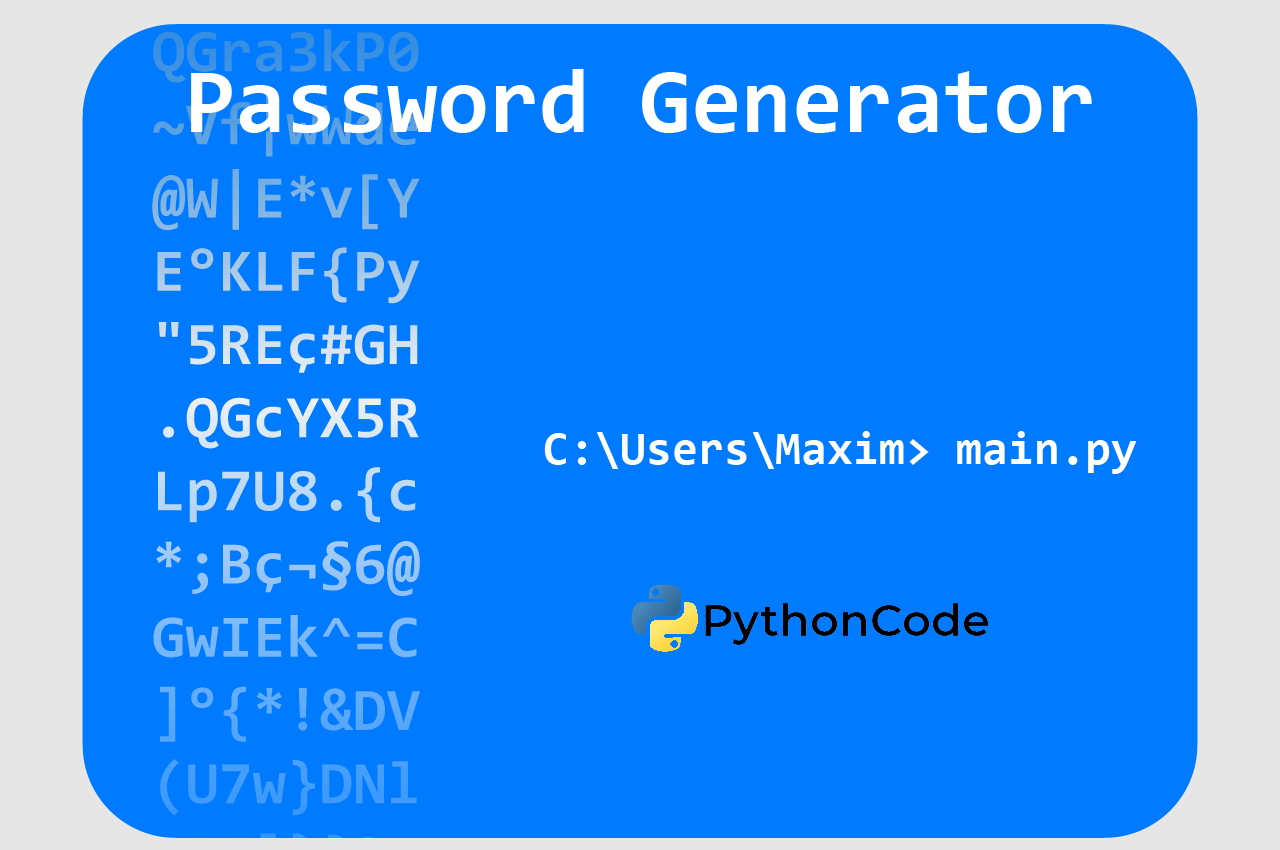
How to Make a Password Generator in Python
Learn how to make a password generator in Python with the ability to choose the length of each character type using the built-in random, string and argparse modules.
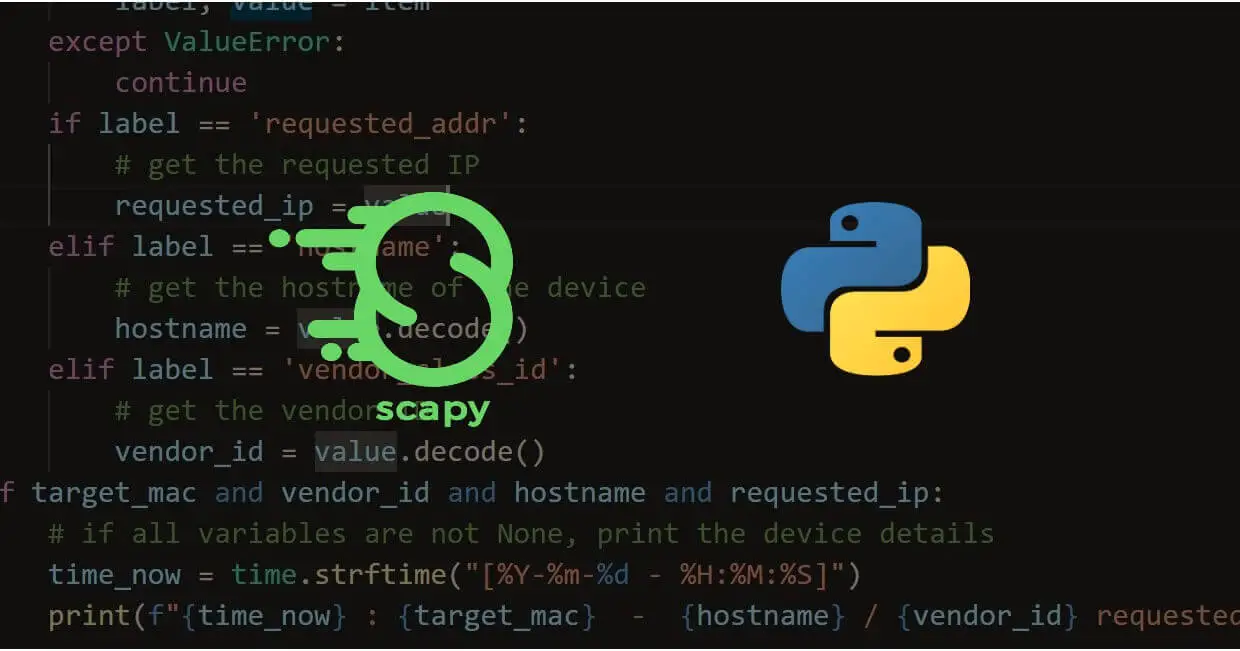
How to Make a DHCP Listener using Scapy in Python
Learn how you can make a DHCP listener by sniffing DHCP packets in the network using the Scapy library in Python.
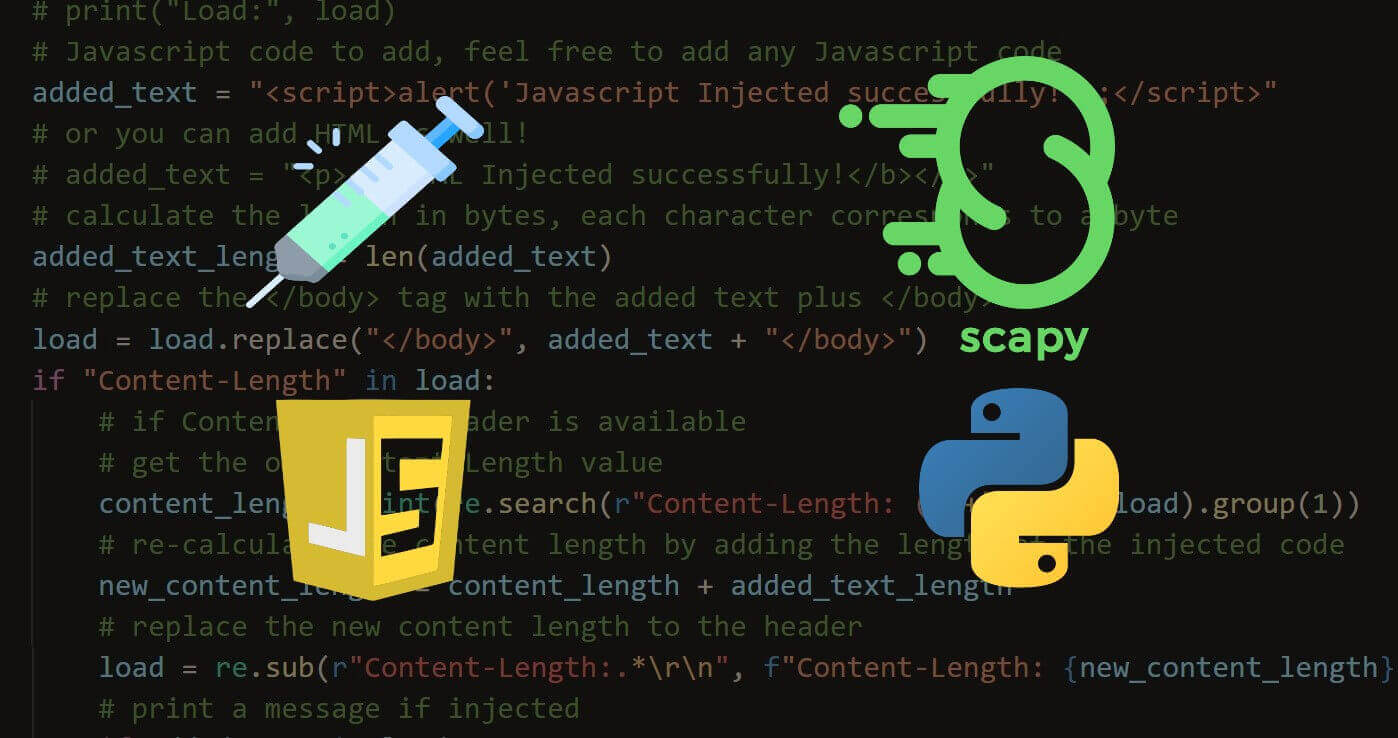
How to Inject Code into HTTP Responses in the Network in Python
Learn how you can inject Javascript, HTML or CSS to HTTP response packets in a spoofed network using Scapy and NetfilterQueue in Python.
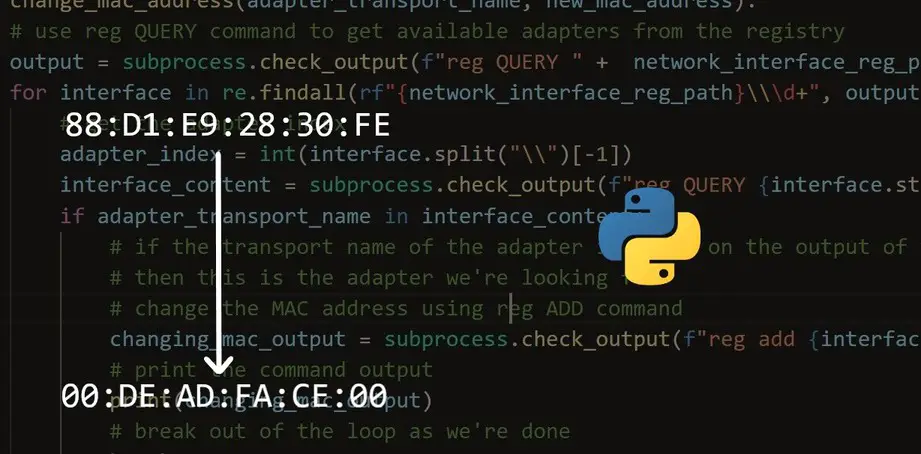
How to Make a MAC Address Changer in Python
Learn how you to make a MAC address changer in Windows and Linux using the subprocess module in Python.
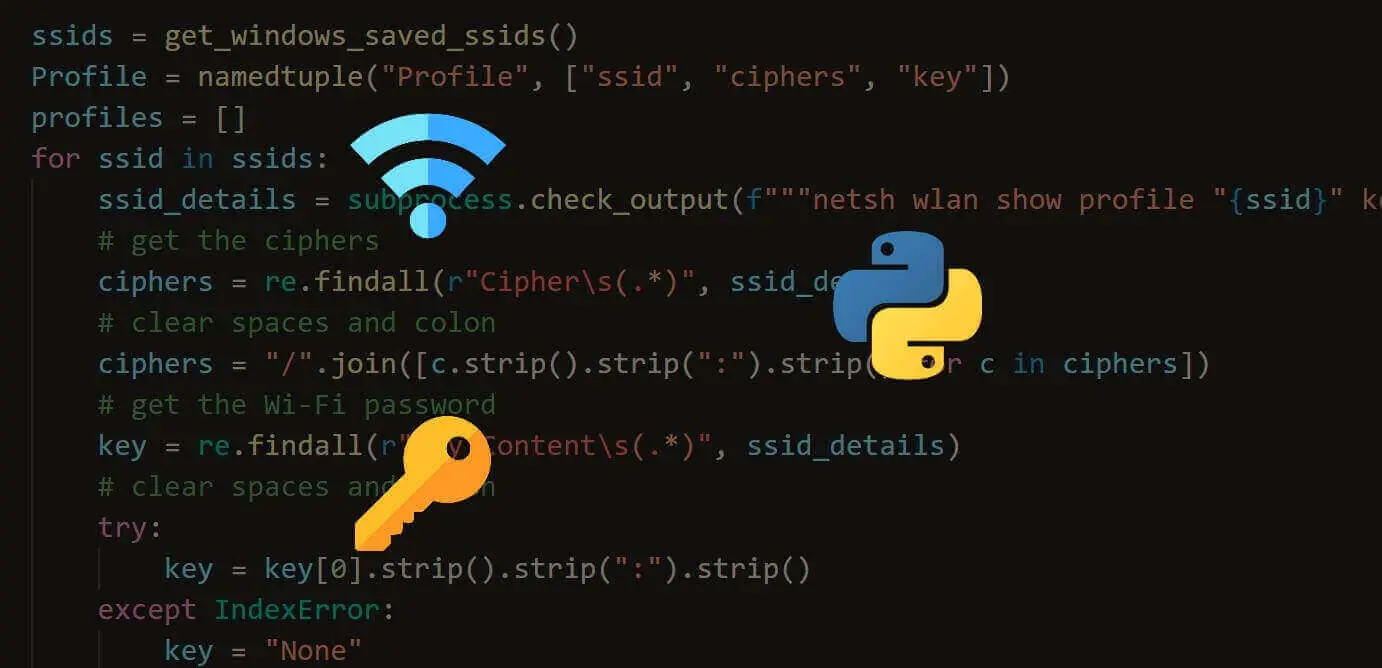
How to Extract Saved WiFi Passwords in Python
Learn how you can extract Wi-Fi passwords that are saved in your machine (either Windows or Linux) using Python without installing any third-party library.
How to Extract Chrome Cookies in Python
Learn how to extract Google Chrome browser saved cookies and decrypt them on your Windows machine in Python.
How to Make an HTTP Proxy in Python
Learn how to use mitmproxy framework to build HTTP proxies using Python
How to Use Shodan API in Python
Learn how to use Shodan API to make a script that searches for public vulnerable servers, IoT devices, power plants and much more using Python.
How to Extract Chrome Passwords in Python
Learn how to extract and decrypt Google Chrome browser saved passwords using Python with the help of sqlite3 and other modules.
How to Make a SYN Flooding Attack in Python
Learn how to use Scapy library in Python to perform a TCP SYN Flooding attack, which is a form of denial of service attacks.
How to Get Domain Name Information in Python
Learn how to validate domain names using WHOIS, as well as getting domain name information such as domain registrar, creation date, expiration date and more in Python.
How to Build a SQL Injection Scanner in Python
Learn how to write a simple Python script to detect SQL Injection vulnerability on web applications using requests and BeautifulSoup in Python.
How to Crack PDF Files in Python
Learn how you can use pikepdf, pdf2john and other tools to crack password protected PDF files in Python.