- Import the Certificate as a Trusted Certificate
- How to import a CA root certificate into the JVM trust store
- Instructions for importing a CA root certificate into the JVM trust store
- Step 1. Obtain the root certificate
- Step 2. Convert the root certificate to DER format
- Step 3. Validate the root certificate content
- Step 4. Import the root certificate into the JVM trust store
- Step 5. Verify that the root certificate has been imported
- How to Add SSL or TLS Certificate in Java
- Why Insert SSL certificate in Java
- Insert SSL Certificate in Java Keystore
- Get the Host Certificate
- Add it to Java Truststore cacert
- Create your Truststore with keytool
- Conclusion
Import the Certificate as a Trusted Certificate
Before you can grant the signed code permission to read a specified file, you need to import Susan’s certificate as a trusted certificate in your keystore.
Suppose that you have received from Susan
- the signed JAR file sCount.jar , which contains the Count.class file, and
- the file Example.cer , which contains the public key certificate for the public key corresponding to the private key used to sign the JAR file.
Even though you created these files and they haven’t actually been transported anywhere, you can simulate being someone other than the creator and sender, Susan. Pretend that you are now Ray. Acting as Ray, you will create a keystore named exampleraystore and will use it to import the certificate into an entry with an alias of susan .
A keystore is created whenever you use a keytool command specifying a keystore that doesn’t yet exist. Thus we can create the exampleraystore and import the certificate via a single keytool command. Do the following in your command window.
- Go to the directory containing the public key certificate file Example.cer . (You should actually already be there, since this lesson assumes that you stay in a single directory throughout.)
- Type the following command on one line:
keytool -import -alias susan -file Example.cer -keystore exampleraystore
Since the keystore doesn’t yet exist, it will be created, and you will be prompted for a keystore password; type whatever password you want.
The keytool command will print out the certificate information and ask you to verify it, for example, by comparing the displayed certificate fingerprints with those obtained from another (trusted) source of information. (Each fingerprint is a relatively short number that uniquely and reliably identifies the certificate.) For example, in the real world you might call up Susan and ask her what the fingerprints should be. She can get the fingerprints of the Example.cer file she created by executing the command
keytool -printcert -file Example.cer
If the fingerprints she sees are the same as the ones reported to you by keytool , the certificate has not been modified in transit. In that case you let keytool proceed with placing a trusted certificate entry in the keystore. The entry contains the public key certificate data from the file Example.cer and is assigned the alias susan .
Previous page: Observe the Restricted Application
Next page: Set Up a Policy File to Grant the Required Permission
How to import a CA root certificate into the JVM trust store
Web browsers and application runtimes, such as Java, have a special local database of recognised Certificate Authorities (CA). Each time an SSL/TLS connection is made, that database is queried in order to validate a server’s claimed identity (typically represented by its domain name).
If you try to make a secure connection (e.g. HTTPS or LDAPS) and the server doesn’t respond with a certificate issued by a recognised authority, the connection will fail with the following exception:
CertPathBuilderException: unable to find valid certification path to requested target If your company has its own CA, or, if you want to make SSL/TLS connections to a server in possession of a certificate issued by a CA which you recognise and trust, but is not listed in the default Java trust store, you will need to import the CA’s root certificate.
We recently encountered such a case when a user of the online OpenID Connect client was not able to connect to a web server which has a certificate issued by the StartCom CA. The root certificate of StartCom is recognised by browsers, but for some reason has not been included in the default JVM trust store.
Instructions for importing a CA root certificate into the JVM trust store
Step 1. Obtain the root certificate
For StartCom the root certificate was made available at http://www.startssl.com/certs/ca.pem, in PEM format. Certificates contain public information and CAs always make them available for download.
Step 2. Convert the root certificate to DER format
This can be done with help of the openssl toolkit, where ca.pem is the original certificate filename in PEM format, and ca.der the filename to output, in DER format (which the Java keytool utility can understand). If you were able to obtain the root certificate in DER format, skip this step.
openssl x509 -in ca.pem -inform pem -out ca.der -outform der Step 3. Validate the root certificate content
Ensure that the Java keytool can parse the certificate and display its content:
keytool -v -printcert -file ca.der Step 4. Import the root certificate into the JVM trust store
Enter the following command where $JAVA_HOME is a shell environment variable that points to your Java installation, e.g. to /usr/lib/jvm/java-7-oracle ; for -alias pick some unique name for the certificate in the store:
keytool -importcert -alias startssl -keystore $JAVA_HOME/jre/lib/security/cacerts -storepass changeit -file ca.der (the default password for the CA store is changeit )
The keytool will prompt you for confirmation, enter yes to complete the operation.
Step 5. Verify that the root certificate has been imported
To do that list the trust store content and filter for the certificate alias (name) with grep :
keytool -keystore "$JAVA_HOME/jre/lib/security/cacerts" -storepass changeit -list | grep startssl You will now be able to make secure SSL/TLS connections to servers which have a certificate signed by the CA which we just imported.
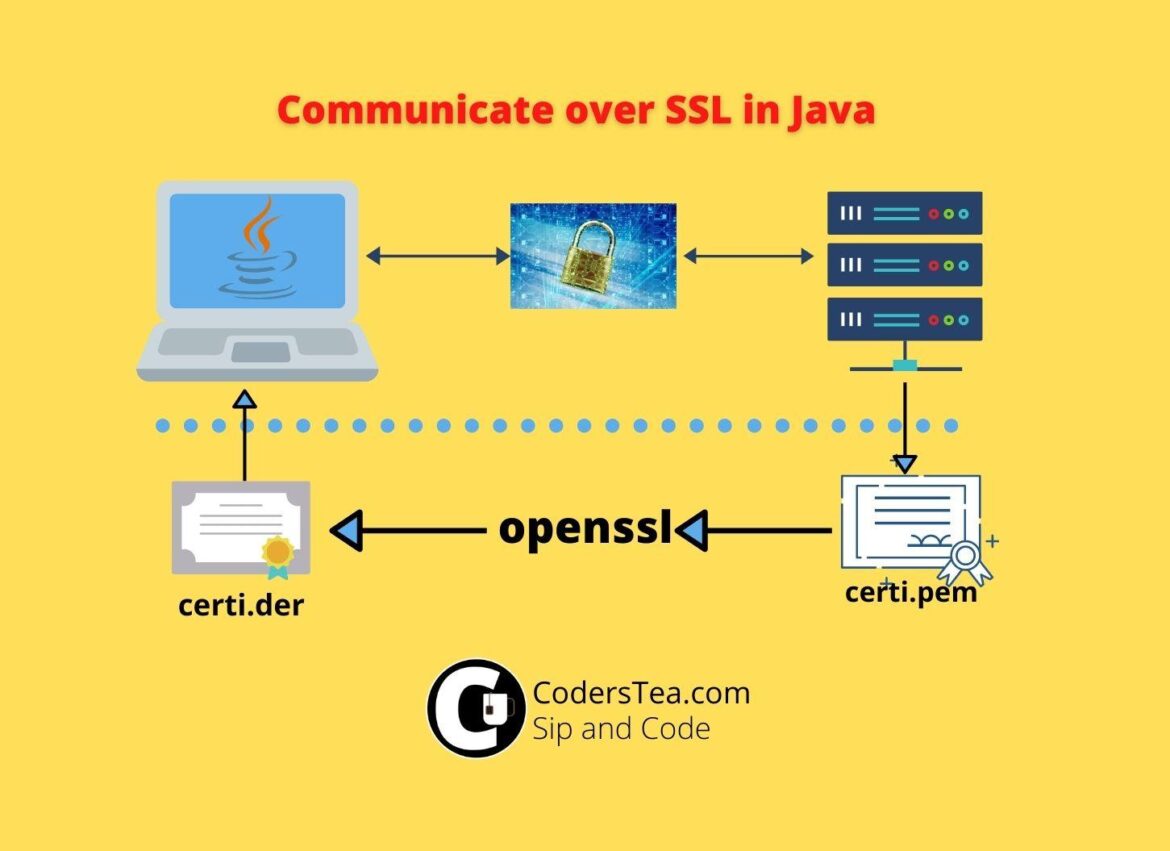
How to Add SSL or TLS Certificate in Java
Hey, Tea Lovers! Today we are going to set up the SSL or TLS certificate for securing our communication with another server. If your Java code is trying to connect to DB over SSL\TLS or calling an HTTPS API then you will be needing that server’s root certificate. We will add SSL or TLS Certificate in Java.
Let’s connect on social media via @coderstea on Twitter, Linkedin, Facebook, or Instagram. We also share high-quality videos about programming on our YouTube channel. Let us help you publish your own post on CodersTea, just share your thought on Contact Us or let us know in the comments or described social media.
To add a certificate via a keytool you have the following options.
Why Insert SSL certificate in Java
When communicating over SSL or TLS Java authenticates the host. If you don’t tell Java that I trust this host then it will throw the following error.
Exception in thread "main" javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested targetCode language: CSS (css)This issue is when Java doesn’t trust the host.
Insert SSL Certificate in Java Keystore
For it to trust it you need to add a host certificate into Java’s Truststore which tells Java that, you trust this host. Let’s look at the steps now.
Get the Host Certificate
First, you have to get the host certificate. You need .cer or .der file. But If you have a .pem file then you have to convert it into .der. Either you can do it online or if you have OpenSSL then you can run the following command.
openssl x509 -in server-certi.pem -inform pem -out server-certi.der -outform derCode language: CSS (css)Add it to Java Truststore cacert
Now that we have got the file, we need to insert it into the truststore. We have to add it to the cacerts of Java.
keytool -import -alias server-name-certi -keystore $JAVA_HOME/jre/lib/security/cacerts -trustcacerts -file /path/to/server-crti.der -storepass changeit -nopromptCode language: JavaScript (javascript)changeit is the default password for the truststore. Replace $JAVA_HOME with the java home if you don’t have that value set up already, or you can set it up with the help of this post. -noprompt is for skipping confirmation.
Create your Truststore with keytool
Sometimes you dint have access or permission to the default truststore. In this case, you can create your own and pass it to the Java VM at runtime.
You can do it via code also, but we will stick to the keytool for now. First, run the following command. You will be needing the .der file.
keytool -keystore customstore -import -alias server-name-certi -file /path/to/server-crti.derCode language: JavaScript (javascript)It will prompt you for a password, then reconfirm the password, and in the end type yes for confirmation to add the certificate. in case you want to skip the input part then you can use the following. But it doesn’t work on windows.
printf 'Mypassword\nMypassword\nyes\n' | keytool -keystore customstore -import -alias server-name-certi -file /path/to/server-crti.derCode language: JavaScript (javascript)After successfully creating the store, it will create a file with the same name as the truststore, customstore in our case, in the same working directly. I will suggest it to create it from where you will be running the java command. you will need to pass it to the Java VM args as the following.
-Djavax.net.ssl.trustStore=customstore -Djavax.net.ssl.trustStorePassword=MypassTherefore, while running the java code or jar file it will look like the following.
java -Djavax.net.ssl.trustStore=customstore -Djavax.net.ssl.trustStorePassword=Mypass Hellojava -Djavax.net.ssl.trustStore=customstore -Djavax.net.ssl.trustStorePassword=Mypass -jar myapplication.jarIf you are running via IDE, then pass it to the run configuration > VM arguments.
Conclusion
We looked at adding the server’s SSL certificate to Java so that it doesn’t throw an SSL Exception. We discussed both the default Java truststore and created a custom one for our use.
In the next post, we will have a look at the DB communication of MySQL and Postgres over SSL and TLS and then how we can add it to Docker to mimic the same.
checkout the other post from CodersTea and all our code at GitHub:
See you in the next post. HAKUNA MATATA.
Let’s connect on social media via @coderstea on Twitter, Linkedin, Facebook, or Instagram. We also share high-quality videos about programming on our YouTube channel. Let us help you publish your own post on CodersTea, just share your thought on Contact Us or let us know in the comments or described social media.
Imran Shaikh
Lead Software Engineer, who is wandering the web. Love to share some insights and my personal opinion on this platform. Let’s connect!!